- Guia: https://www.cyberciti.biz/faq/set-up-a-firewall-with-ufw-on-debian-12-linux/
- Actualizamos
apt update
apt upgrade- Instalamos
apt install ufw -y
// Verificar
ufw version
// Resultado
ufw 0.36.2
Copyright 2008-2023 Canonical Ltd.- Ahora debemos habiltar el servicio
//habilitar
ufw enable
//Deshabilitar
ufw disable- Respuesta, nos muestra un mensaje que debemos confirmar
Command may disrupt existing ssh connections. Proceed with operation (y|n)? y
Firewall is active and enabled on system startup- Ahora poemos verificar el estado, reinicar y demas
//***************************
// Consultar estado
//***************************
systemctl status ufw.service
//***************************
// Detener Servicio
//***************************
ufw disable
//***************************
//verbose: Lista Reglas
//***************************
ufw status
//---------------------------
// Respuesta
//---------------------------
//***************************
//verbose: Lista Reglas
//***************************
ufw status verbose
//---------------------------
// Respuesta
//---------------------------
Status: active
Logging: on (low)
Default: deny (incoming), allow (outgoing), disabled (routed)
New profiles: skip
//***************************
//numbered: Lista Reglas
//***************************
sudo ufw status numbered
//---------------------------
// Respuesta
//---------------------------
Status: active- Ahora le aplicamos las reglas necesarias
Ejemplos de Reglas
SSH
- Habilitar ssh en puerto defecto
ufw allow ssh- Habilitar si esta en un puerto distinto
ufw allow 44/tcpHTTP / HTTPS 80/443
- Habilitamos los defectos
ufw allow http
ufw allow httpsOtros
- De una red a otra por un puerto específico
ufw allow proto tcp from 103.1.2.3 to 139.144.1.2 port 22
ufw allow from 192.168.100.52 proto tcp to any portComandos
Consultar reglas
- Consultar reglas agregadas
ufw show added- Resultado
Consultar Politicas
- Ejecutamos
grep -i '^default_' /etc/default/ufw- Resultado
DEFAULT_INPUT_POLICY="DROP"
DEFAULT_OUTPUT_POLICY="ACCEPT"
DEFAULT_FORWARD_POLICY="DROP"
DEFAULT_APPLICATION_POLICY="SKIP"Cambiar Politicas
- Puede utilizar
ufw default default allow|deny|reject [incoming|outgoing|routed]- Ejemplos
ufw default deny incoming
ufw default allow outgoing- Explicación de las politicas
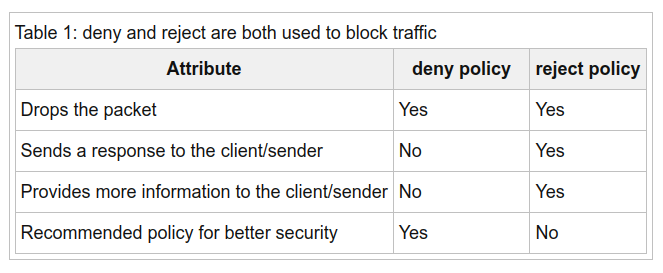
Permitir Una IP o red a Todo
//IP
ufw allow from 1.2.3.4
//RED
ufw allow from 192.168.2.0/24IP a HTTP / HTTPS
ufw allow from 1.2.3.4 to any port 80
ufw allow from 1.2.3.4 to any port 443Multiples puertos
ufw allow proto tcp from 1.2.3.4 to any port 22,80,443
ufw allow from 192.168.100.52 proto tcp to any port 80,443Rango de puertos
ufw allow 3000:4000/tcp
ufw allow 3000:4000/udpBloquear una IP, RED o Puerto Ataque
- Drop
ufw deny from 1.2.3.4
ufw deny from 192.168.5.0/24
ufw deny 23/tcp- Reject
ufw reject from 1.2.3.4
ufw reject from 192.168.5.0/24
ufw reject 23/tcpBloquear Puerto
Puerto completo
ufw deny 25
//red
ufw deny proto tcp from 192.168.1.0/24 port 25Bloquear todo
ufw deny allProteger fuerza bruta
The ufw supports connection rate limiting, which is useful for protecting against brute-force login attacks. When a limit rule is used, ufw will normally allow the connection but will deny connections if an IP address attempts to initiate 6 or more connections within 30 seconds. Typical usage is:
ufw limit ssh/tcpEliminar regla
- Listamos la reglas
ufw status numbered- Indicamos el numero de regla a eliminar
ufw status numbered- Verificar
ufw status numberedEstablecer el orden como deben ejecutarse las reglas
It’s crucial to understand the sequence of ufw rules in the system table, which includes PREROUTING, INPUT, FORWARD, OUTPUT, FORWARD, and POSTROUTING. The order of these rules determines which rule will be executed first when a packet matches. Therefore, it’s possible to add a rule at a specific location using ufw to ensure it’s applied correctly. The syntax is:
sudo ufw insert [position] [rule] Where, the position is the position of the rule in the chain. The position can be a number, such as 1. The rule is the rule that you want to insert or delete. The rule can be a simple rule, such as allow ssh, or a more complex rule as per your needs
ufw insert 1 allow 25/tcp- Podemos crear así la reglas para que se inserte de primero
ufw prepend deny from 1.2.3.4Habilitar aplicación: NFS para montar discos
- Listar aplicaciones
ufw app list- Habilitar NFS
ufw app info NFS- Deshabilitar
ufw delete allow NFSVer puertos escuchando
ufw show listening