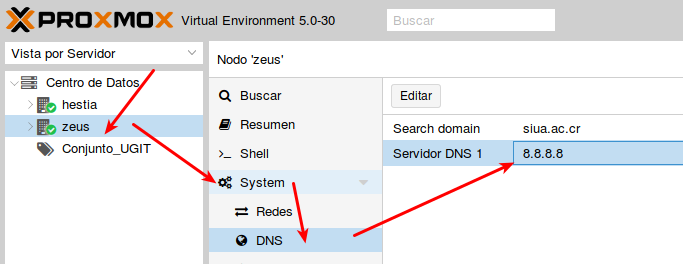
- Paso 0: requisitos:
- Paso 0.1: instalar apache
apt install apache2
- Paso 0.2: en la interfaz web «Centro de Datos->nodo->System->DNS» y editarlo por el de google
- Paso 0.3: NOTA: asegure que en «Centro de Datos->nodo->Redes-Inicio Automatico» de todas las interfaces están en YES
- Paso 0.4: asegure que puede ingresar desde una red publica al servidor
- Paso 1: ingresar a la terminal del servidor
- Paso 2: Ubicarnos en la carpeta
- Paso 3: Instalar el cerbot
apt-get install certbot python-certbot-apache
- Ahora vamos a crear un virtual host par a que soporte el nombre de todos los nodos
- Creamos el archivo de nombre clusterugit.conf
nano /etc/apache2/sites-available/clusterugit.conf
- Agregamos el siguiente contenido
NameVirtualHost *:80
<VirtualHost *:80>
ServerName ares.siua.ac.cr
</VirtualHost>
<VirtualHost *:80>
ServerName apolo.siua.ac.cr
</VirtualHost>
<VirtualHost *:80>
ServerName hades.siua.ac.cr
</VirtualHost>
<VirtualHost *:80>
ServerName hestia.siua.ac.cr
</VirtualHost>
<VirtualHost *:80>
ServerName metis.siua.ac.cr
Redirect / https://metis.siua.ac.cr:8006
</VirtualHost>
<VirtualHost *:80>
ServerName selene.siua.ac.cr
</VirtualHost>
<VirtualHost *:80>
ServerName poseidon.siua.ac.cr
</VirtualHost>
<VirtualHost *:80>
ServerName zeus.siua.ac.cr
</VirtualHost>
- Habilitamos el virtual host
a2ensite clusterugit.conf
- Paso 5: Solicitamos el certificado
certbot certonly --apache
Si es la primera vez que se ejecuta
- Escoger la opción: «Apache Web Server plugin – Beta (apache)» ->2
- PREGUNTA:
How would you like to authenticate with the ACME CA?
-------------------------------------------------------------------------------
1: Apache Web Server plugin - Beta (apache)
2: Spin up a temporary webserver (standalone)
3: Place files in webroot directory (webroot)
-------------------------------------------------------------------------------
Select the appropriate number [1-3] then [enter] (press 'c' to cancel): 1
- LetsEncrypt necesita un correo para el envió de notificaciones
Enter email address (used for urgent renewal and security notices) (Enter 'c' to
cancel): interuniversitariadealajuela@gmail.com
- Aceptamos los términos de licencia
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.1.1-August-1-2016.pdf. You must agree
in order to register with the ACME server at
https://acme-v01.api.letsencrypt.org/directory
-------------------------------------------------------------------------------
(A)gree/(C)ancel: A
- No pregunta si deseamos suscribirnos con Electronic Frontier Foundation -> N
Would you be willing to share your email address with the Electronic Frontier
Foundation, a founding partner of the Let's Encrypt project and the non-profit
organization that develops Certbot? We'd like to send you email about EFF and
our work to encrypt the web, protect its users and defend digital rights.
-------------------------------------------------------------------------------
(Y)es/(N)o: N
- Nos dice que el certificado se configuro correctamente
Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/poseidon.siua.ac.cr/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/poseidon.siua.ac.cr/privkey.pem
Your cert will expire on 2018-02-01. To obtain a new or tweaked
version of this certificate in the future, simply run certbot-auto
again. To non-interactively renew *all* of your certificates, run
"certbot-auto renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
Si no es la primera vez
- Seleccionamos todos los dominios
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator apache, Installer apache
Which names would you like to activate HTTPS for?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: apolo.siua.ac.cr
2: ares.siua.ac.cr
3: hades.siua.ac.cr
4: hestia.siua.ac.cr
5: metis.siua.ac.cr
6: poseidon.siua.ac.cr
7: selene.siua.ac.cr
8: zeus.siua.ac.cr
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate numbers separated by commas and/or spaces, or leave input
blank to select all options shown (Enter 'c' to cancel): 1 2 3 4 5 6 7 8
Obtaining a new certificate
Performing the following challenges:
http-01 challenge for metis.siua.ac.cr
Waiting for verification...
Cleaning up challenges
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem
Your cert will expire on 2020-04-12. To obtain a new or tweaked
version of this certificate in the future, simply run certbot
again. To non-interactively renew *all* of your certificates, run
"certbot renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
Continuamos…
- Respaldamos los certificados
cp /etc/pve/local/pve-ssl.pem /etc/pve/local/pve-ssl.pem.bak
cp /etc/pve/local/pve-ssl.key /etc/pve/local/pve-ssl.key.bak
cp /etc/pve/pve-root-ca.pem /etc/pve/pve-root-ca.pem.bak
- Copiamos los nuevos certificados a todos los nodos
#METIS
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/metis/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/metis/pveproxy-ssl.key
#APOLO
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/apolo/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/apolo/pveproxy-ssl.key
#HESTIA
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/hestia/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/hestia/pveproxy-ssl.key
- Reiniciamos el servicio web (pveproxy) para que aplique los cambios
service pveproxy restart
- Para que la renovación sea automática, vamos a crear un archivo que se ejecute mensualmente y renueve los certificados
- Creamos el archivo en el nodo master
nano /root/ssh-renew.sh
- Paso 10: agregue el siguiente código
#******************************************************************************************************************************
#*********************************** RENOVADO CERTIFICADOS ***********************************************
#******************************************************************************************************************************
printf "******************************************\n"
printf "********** RENOVANDO CERTIFICADOS ********\n"
printf "******************************************\n"
certbot renew --dry-run
#******************************************************************************************************************************
#*********************************** SERVIDORES ***********************************************
#******************************************************************************************************************************
printf "******************************************\n"
printf "********** METIS ********\n"
printf "******************************************\n"
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/metis/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/metis/pveproxy-ssl.key
service pveproxy restart
printf "******************************************\n"
printf "********** APOLO ********\n"
printf "******************************************\n"
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/apolo/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/apolo/pveproxy-ssl.key
#Reiniciar el servicio
ssh root@apolo.siua.ac.cr service pveproxy restart
printf "******************************************\n"
printf "********** HESTIA ********\n"
printf "******************************************\n"
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/apolo/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/apolo/pveproxy-ssl.key
#Reiniciar el servicio
ssh root@hestia.siua.ac.cr service pveproxy restart
- Paso 11: Lo hacemos ejecutable
chmod 755 /root/ssh-renew.sh
- Paso 12: Abrir crontab para ejecutarlo cada 30 dias
crontab -e
@monthly /root/ssh-renew.sh
- Paso 14: como modificamos los certificados en el node «poseidon» y este pertenece a un cluster debemos copiar estos nuevos certificados a todos los ?controller=post&action=list&number=1demás nodos sino da error de certificados al arrancar las máquinas para esto
#METIS
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/metis/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/metis/pveproxy-ssl.key
#Apolo
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/apolo/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/apolo/pveproxy-ssl.key
#Ares
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/ares/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/ares/pveproxy-ssl.key
#Hades
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/hades/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/hades/pveproxy-ssl.key
#Hestia
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/hestia/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/hestia/pveproxy-ssl.key
#Poseidon
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/poseidon/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/poseidon/pveproxy-ssl.key
#Selene
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/selene/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/selene/pveproxy-ssl.key
#Zeus
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/zeus/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/zeus/pveproxy-ssl.key
- Paso 15: como los certificados se vencen cada 19 días modificamos el script de autorenovación para que haga estos cambios
nano /root/ssh-renew.sh
#******************************************************************************************************************************
#*********************************** RENOVADO CERTIFICADOS ***********************************************
#******************************************************************************************************************************
printf "******************************************\n"
printf "********** RENOVANDO CERTIFICADOS ********\n"
printf "******************************************\n"
certbot renew --dry-run
#******************************************************************************************************************************
#*********************************** SERVIDORES ***********************************************
#******************************************************************************************************************************
printf "******************************************\n"
printf "********** METIS ********\n"
printf "******************************************\n"
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/metis/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/metis/pveproxy-ssl.key
#Reinicar servicio
systemctl restart pveproxy
service pveproxy restart
printf "******************************************\n"
printf "********** APOLO ********\n"
printf "******************************************\n"
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/apolo/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/apolo/pveproxy-ssl.key
#Reiniciar el servicio
ssh root@apolo.siua.ac.cr systemctl restart pveproxy
ssh root@apolo.siua.ac.cr service pveproxy restart
printf "******************************************\n"
printf "********** ARES ********\n"
printf "******************************************\n"
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/ares/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/ares/pveproxy-ssl.key
#Reiniciar el servicio
ssh root@ares.siua.ac.cr systemctl restart pveproxy
ssh root@ares.siua.ac.cr service pveproxy restart
printf "******************************************\n"
printf "********** HADES ********\n"
printf "******************************************\n"
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/hades/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/hades/pveproxy-ssl.key
#Reiniciar el servicio
ssh root@hades.siua.ac.cr systemctl restart pveproxy
ssh root@hades.siua.ac.cr service pveproxy restart
printf "******************************************\n"
printf "********** HESTIA ********\n"
printf "******************************************\n"
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/hestia/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/hestia/pveproxy-ssl.key
#Reiniciar el servicio
ssh root@hestia.siua.ac.cr systemctl restart pveproxy
ssh root@hestia.siua.ac.cr service pveproxy restart
printf "******************************************\n"
printf "********** POSEIDON ********\n"
printf "******************************************\n"
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/poseidon/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/poseidon/pveproxy-ssl.key
#Reiniciar el servicio
ssh root@poseidon.siua.ac.cr systemctl restart pveproxy
ssh root@poseidon.siua.ac.cr service pveproxy restart
printf "******************************************\n"
printf "********** SELENE ********\n"
printf "******************************************\n"
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/selene/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/selene/pveproxy-ssl.key
#Reiniciar el servicio
ssh root@selene.siua.ac.cr systemctl restart pveproxy
ssh root@selene.siua.ac.cr service pveproxy restart
printf "******************************************\n"
printf "********** zeus ********\n"
printf "******************************************\n"
cp /etc/letsencrypt/live/apolo.siua.ac.cr/fullchain.pem /etc/pve/nodes/zeus/pveproxy-ssl.pem
cp /etc/letsencrypt/live/apolo.siua.ac.cr/privkey.pem /etc/pve/nodes/zeus/pveproxy-ssl.key
#Reiniciar el servicio
ssh root@zeus.siua.ac.cr systemctl restart pveproxy
ssh root@zeus.siua.ac.cr service pveproxy restart